Introduction:
Welcome to the End-to-End DevSecOps Kubernetes Project guide! In this comprehensive project, we will walk through the process of setting up a robust Three-Tier architecture on AWS using Kubernetes, DevOps best practices, and security measures. This project aims to provide hands-on experience in deploying, securing, and monitoring a scalable application environment.
Project Overview:
In this project, we will cover the following key aspects:
IAM User Setup: Create an IAM user on AWS with the necessary permissions to facilitate deployment and management activities.
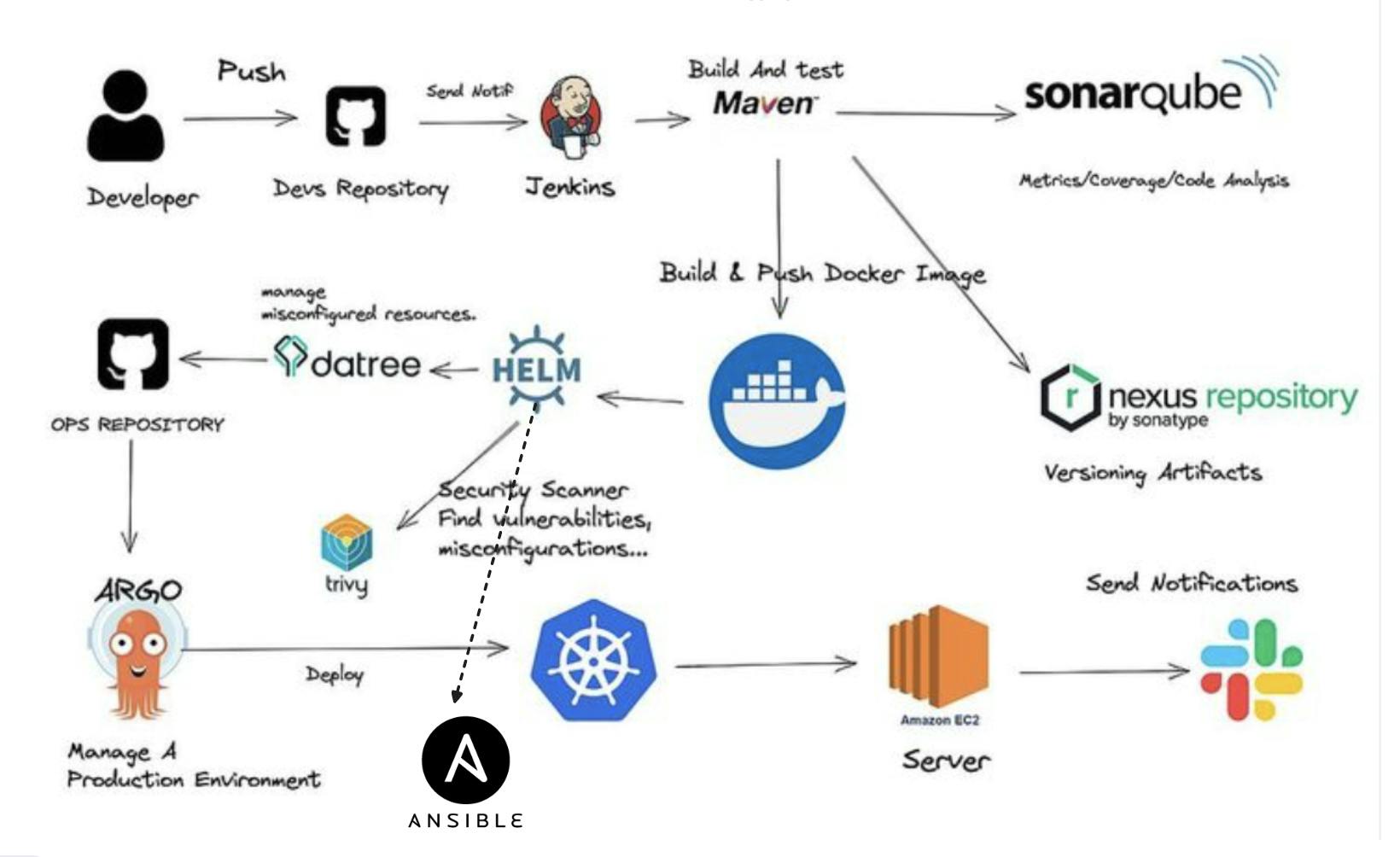
Infrastructure as Code (IaC): Use Terraform and AWS CLI to set up the Jenkins server (EC2 instance) on AWS.
Jenkins Server Configuration: Install and configure essential tools on the Jenkins server, including Jenkins itself, Docker, Sonarqube, Terraform, Kubectl, AWS CLI, and Trivy.
EKS Cluster Deployment: Utilize eksctl commands to create an Amazon EKS cluster, a managed Kubernetes service on AWS.
Load Balancer Configuration: Configure AWS Application Load Balancer (ALB) for the EKS cluster.
Amazon ECR Repositories: Create private repositories for both frontend and backend Docker images on Amazon Elastic Container Registry (ECR).
ArgoCD Installation: Install and set up ArgoCD for continuous delivery and GitOps.
Sonarqube Integration: Integrate Sonarqube for code quality analysis in the DevSecOps pipeline.
Jenkins Pipelines: Create Jenkins pipelines for deploying backend and frontend code to the EKS cluster.
Monitoring Setup: Implement monitoring for the EKS cluster using Helm, Prometheus, and Grafana.
ArgoCD Application Deployment: Use ArgoCD to deploy the Three-Tier application, including database, backend, frontend, and ingress components.
DNS Configuration: Configure DNS settings to make the application accessible via custom subdomains.
Data Persistence: Implement persistent volume and persistent volume claims for database pods to ensure data persistence.
Conclusion and Monitoring: Conclude the project by summarizing key achievements and monitoring the EKS cluster’s performance using Grafana.
etc
Prerequisites:
Before starting the project, ensure you have the following prerequisites:
An AWS account with the necessary permissions to create resources.
Terraform and AWS CLI installed on your local machine.
Basic familiarity with Kubernetes, Docker, Jenkins, and DevOps principles.
Chapters:
Introduction| Part 1
Corporate DevOps Security Tools | Part 2
Trivy Vulnerability Scanner Tool For | Part 3
Real-Time AWS Security DevOps Tool | Part 4
Dockle Container Security Diagnosis | Part 5
Jenkins | Part 5
Kubernetes | Part 6
Nexus | Part 7
Sonarqube | Part 8
Ansible | Part 9
Argo | Part 10
Gitlab | Part 11
Nexus Repository | Part 12
Datree | Part 13
Teraform | Part 14
Grafana | Part 15
Prometheus | Part 16
ELK Stack,
Apache Flink
Kafka
Elasticsearch
Kibana
Docker
Minio
Iceberg
DynamoDB
Furthermore, there are various popular tools integrated such as nmap for network scans, Gitleaks for secrets detections, and much more.